Terraforming Vault: Codify Your Auth with Okta
Adding roles and access policies on an adhoc basis can quickly lead to a situation where you aren’t quite sure who can access what. Building this access into your code is organized, auditable, and makes updating easy.
Here we use Terraform to configure Okta as an OIDC identity provider, mapping groups in Okta to roles in Vault.
Git Repo
All steps are included in the iac-hashicorp-vault Github repository, under the oidc-auth-with-okta lab.
Okta Account
- Start by signing up for an Okta dev account. Once you’re inside, navigate to the admin section.
- Create a group called
admin-groupand put your user inside that group.
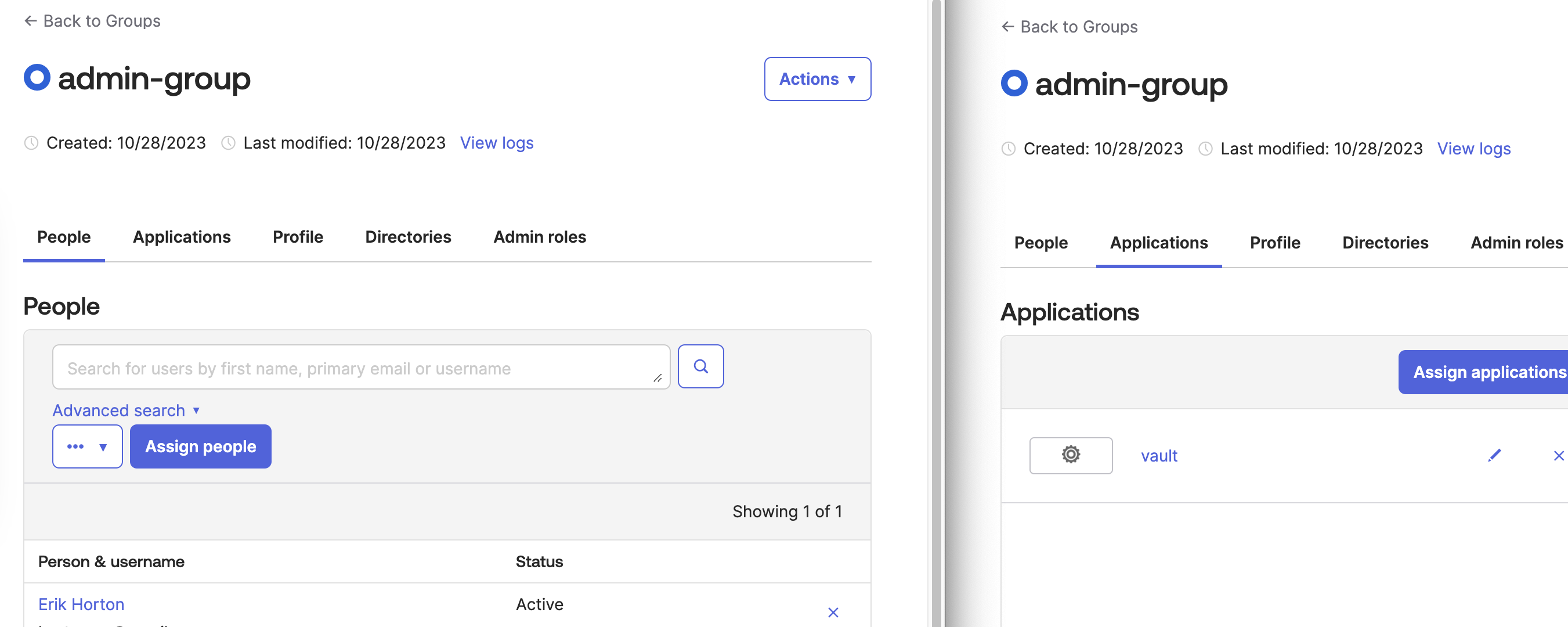
- Create an application, following the steps in the Github repository.
- When you’re done, your application should be configured like the following:
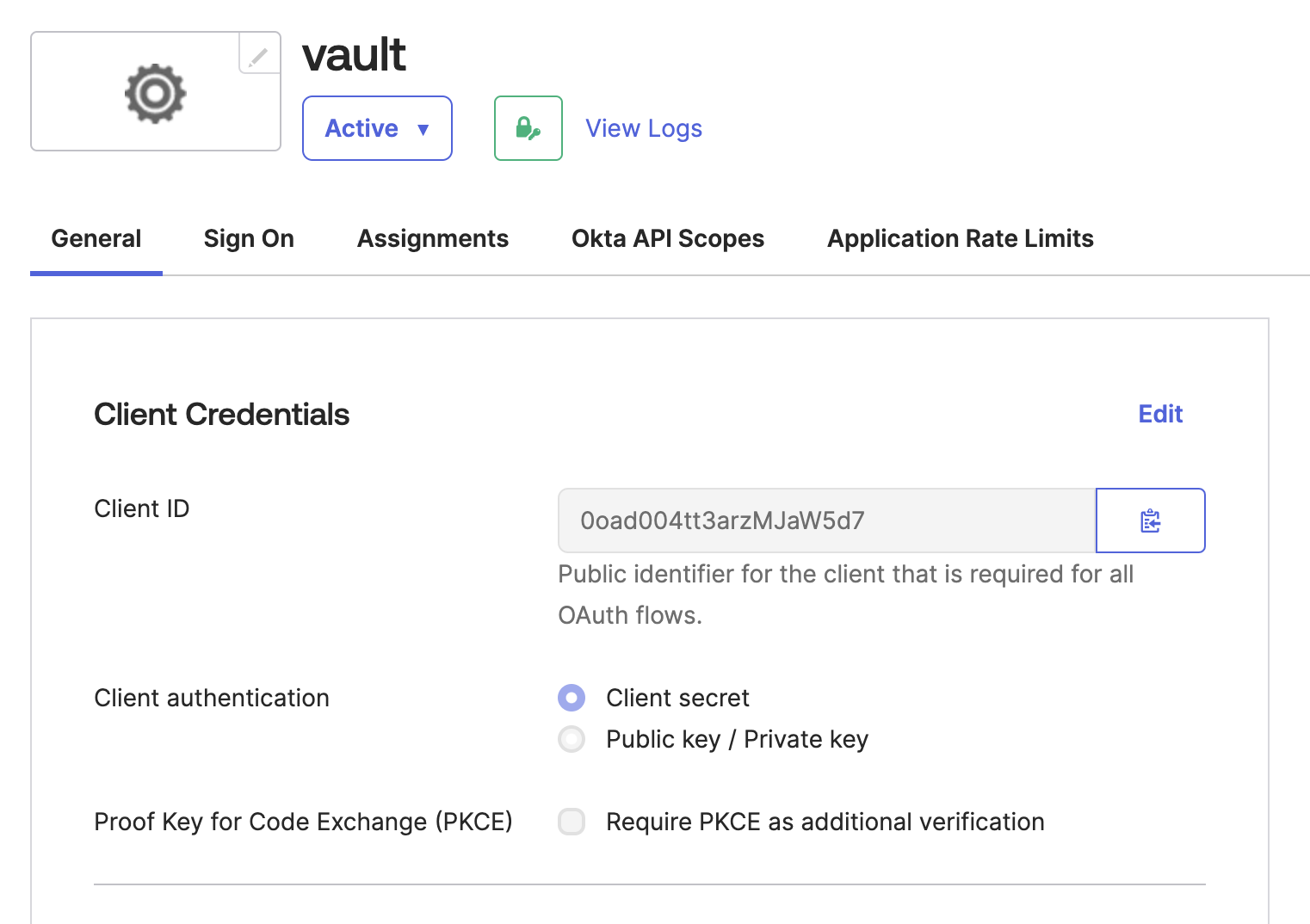
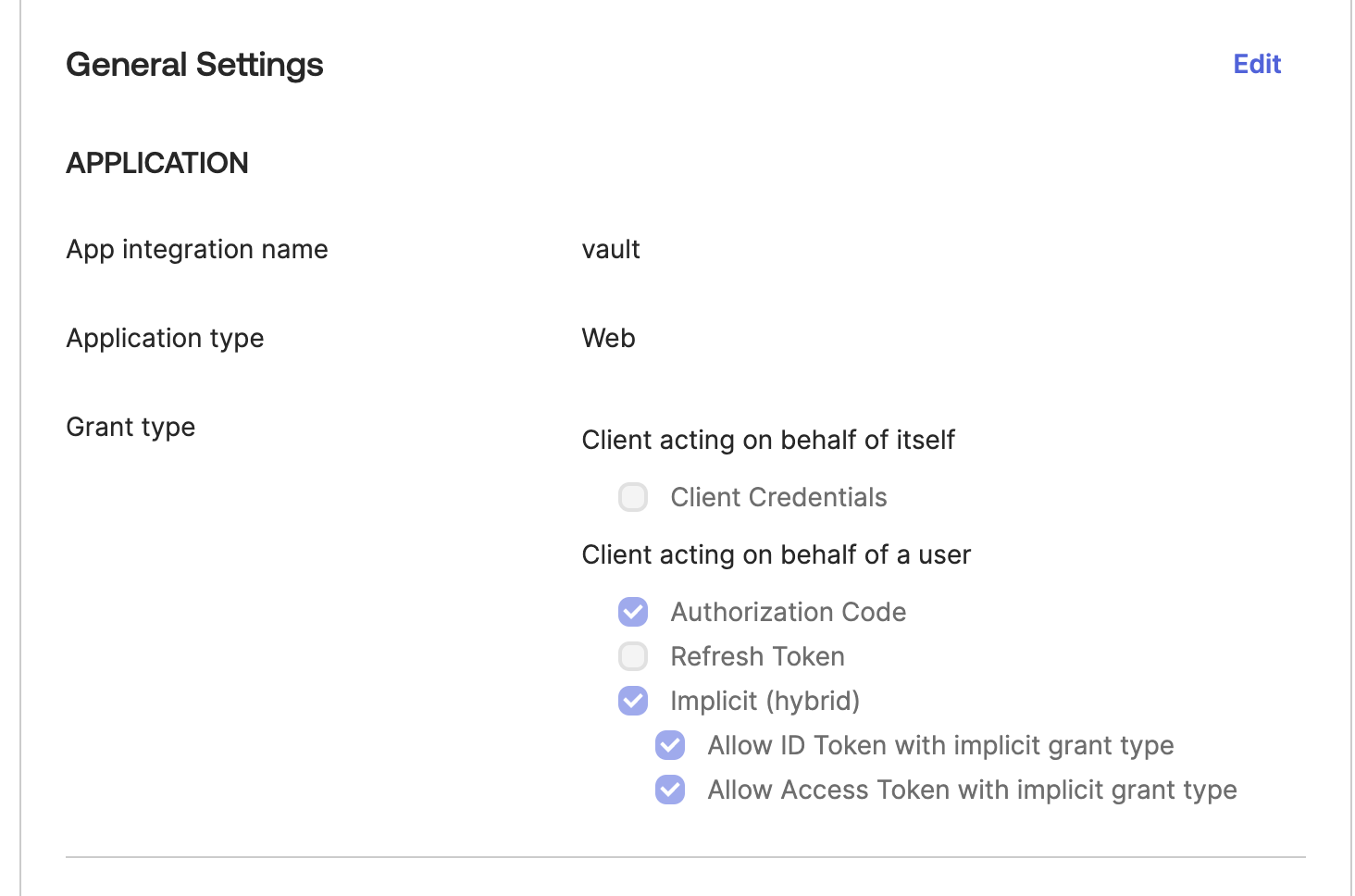
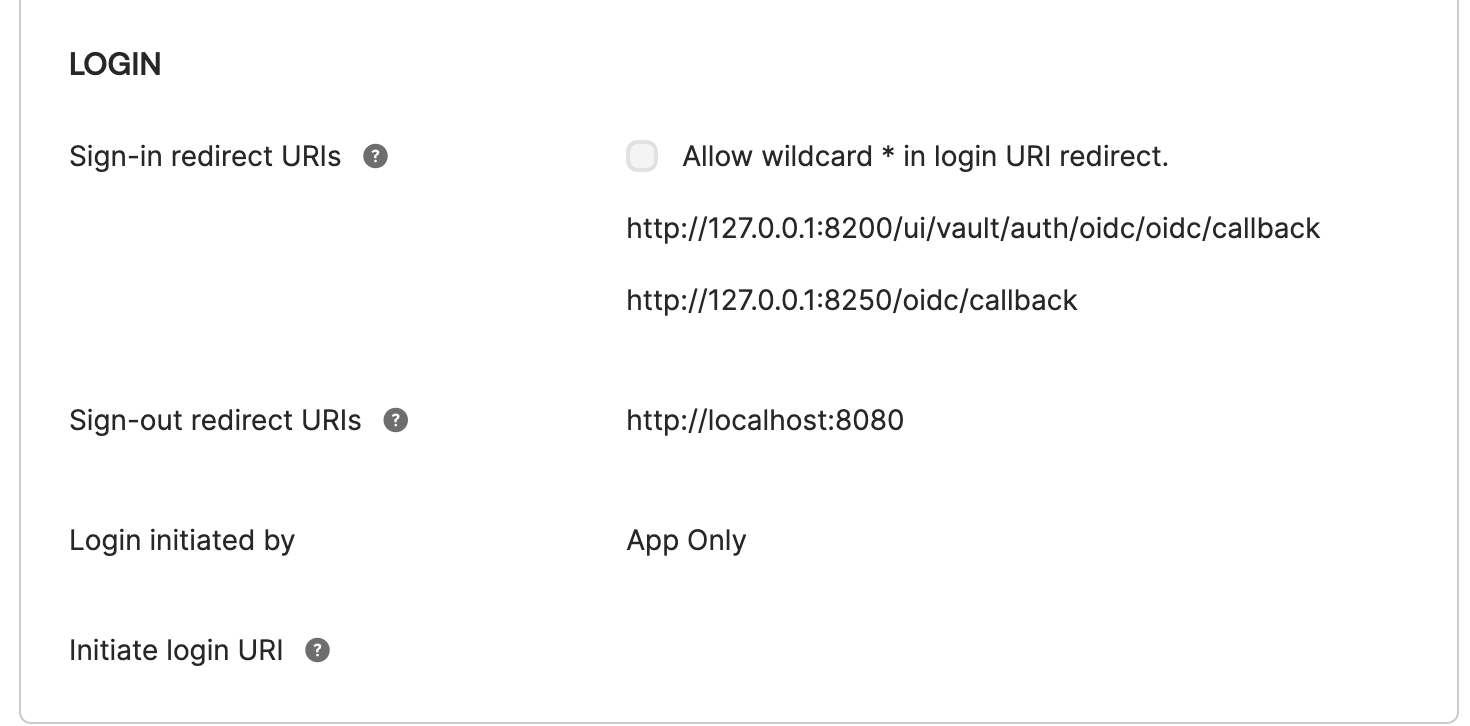
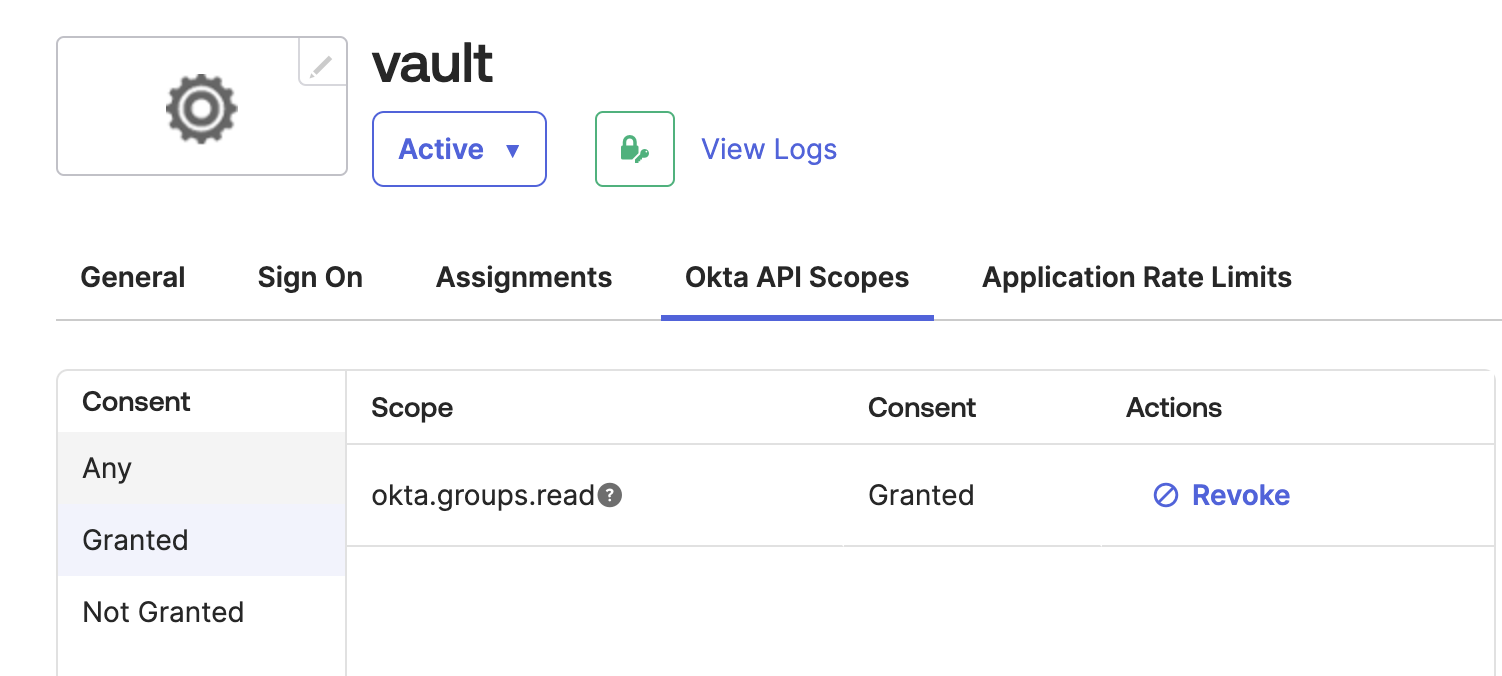
You now have an application with a client ID and secret that will enable Vault to verify users and map them to roles.
Kubernetes + Vault
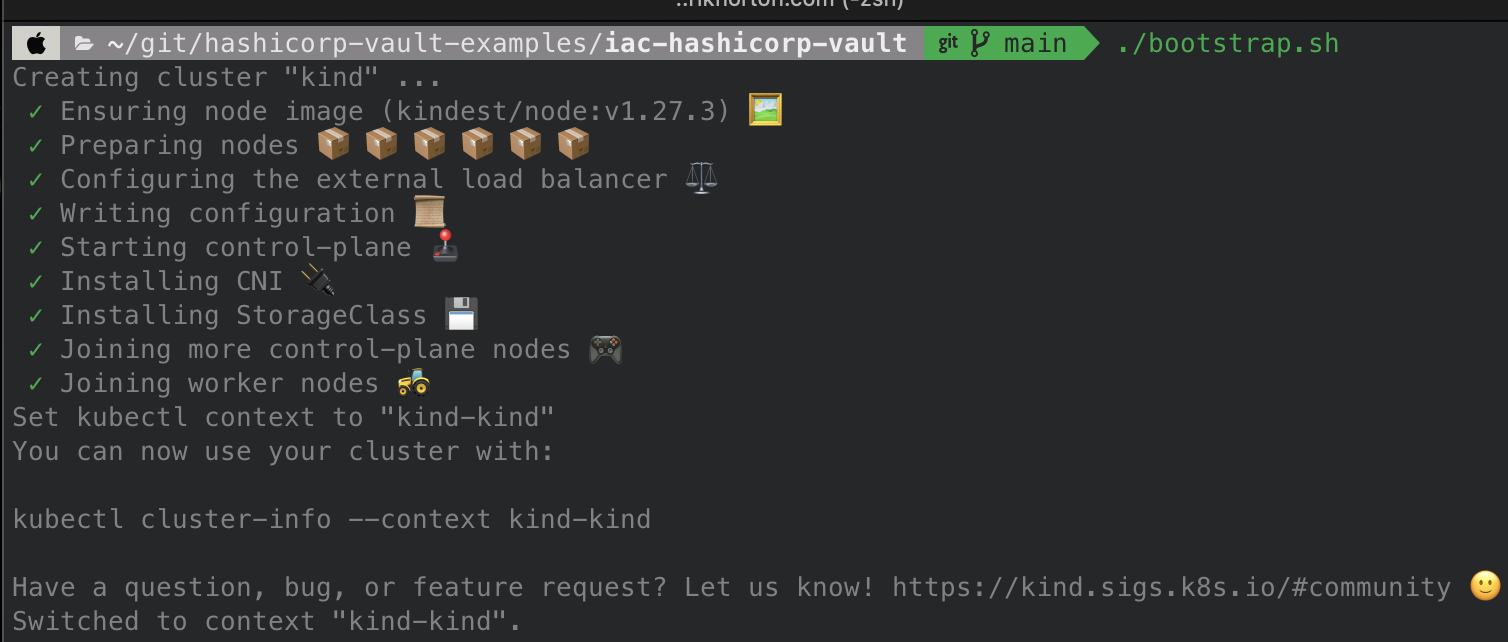
Follow the instructions in the repository’s readme, where you bootstrap a new local environment to run labs on.
- The kind cluster is set up
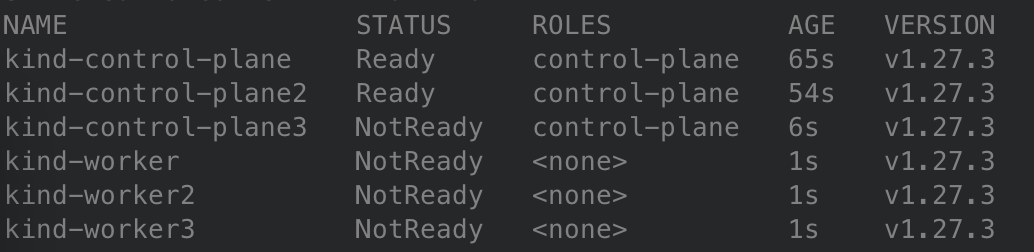
- The nodes begin to come online
- Vault is installed via Helm
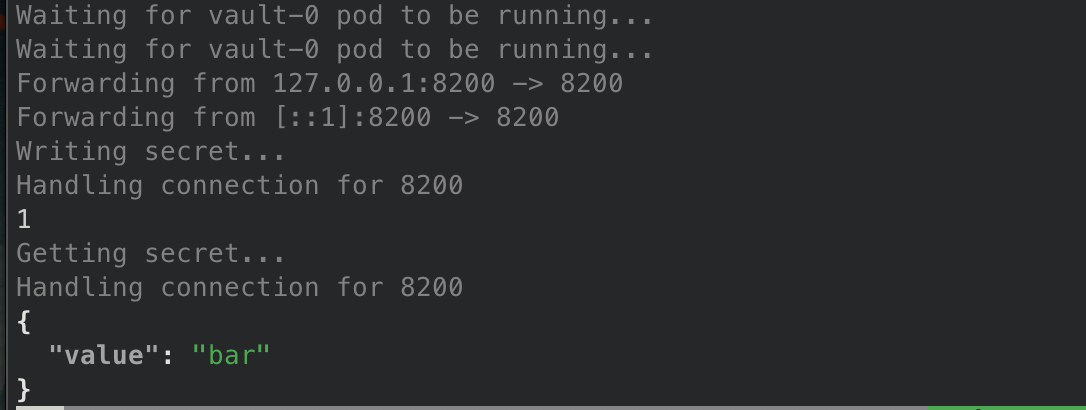
- Curl is used to confirm we can reach the Vault API
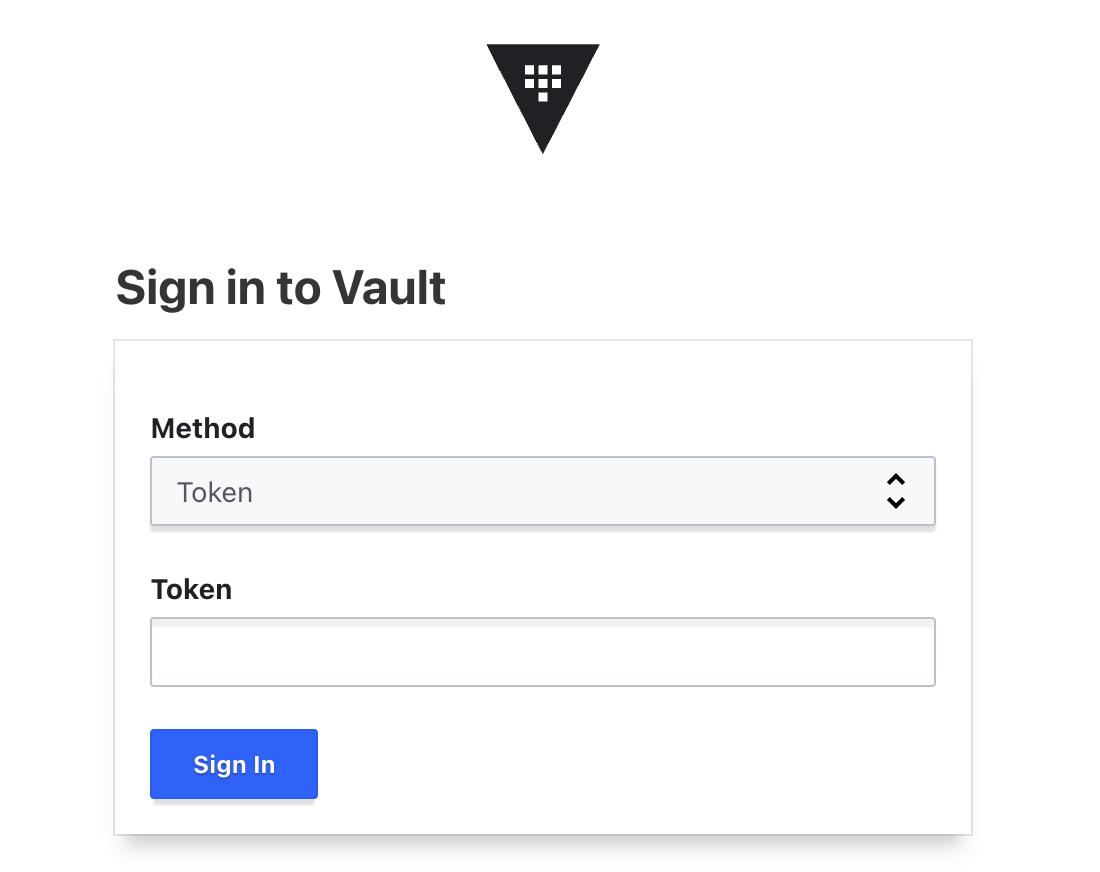
- You should now be able to get to http://127.0.0.1:8200 to sign in.
Terraform
Follow the instructions in the oidc-auth-with-okta lab, setting up:
- terraform.tfvars for: okta_base_url_full, okta_client_id
- environment variables for: VAULT_ADDR, VAULT_TOKEN, TF_VAR_okta_client_secret
Apply the terraform to configure the authentication provider, policies, and roles.
- Terraform init
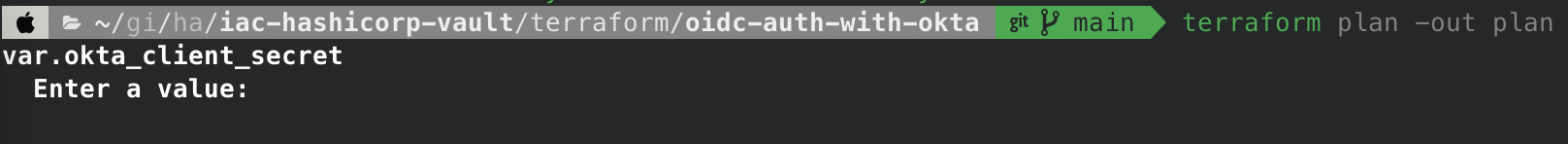
- Terraform plan: notice if you didn’t export
TF_VAR_okta_client_secretit will prompt you for it here.
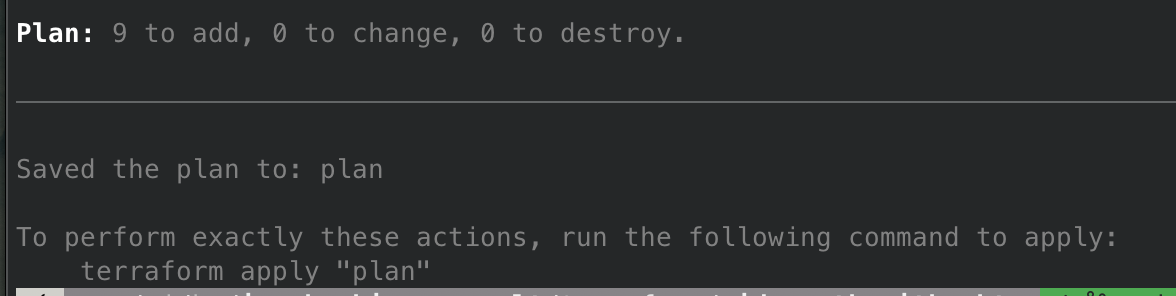
- Terraform apply
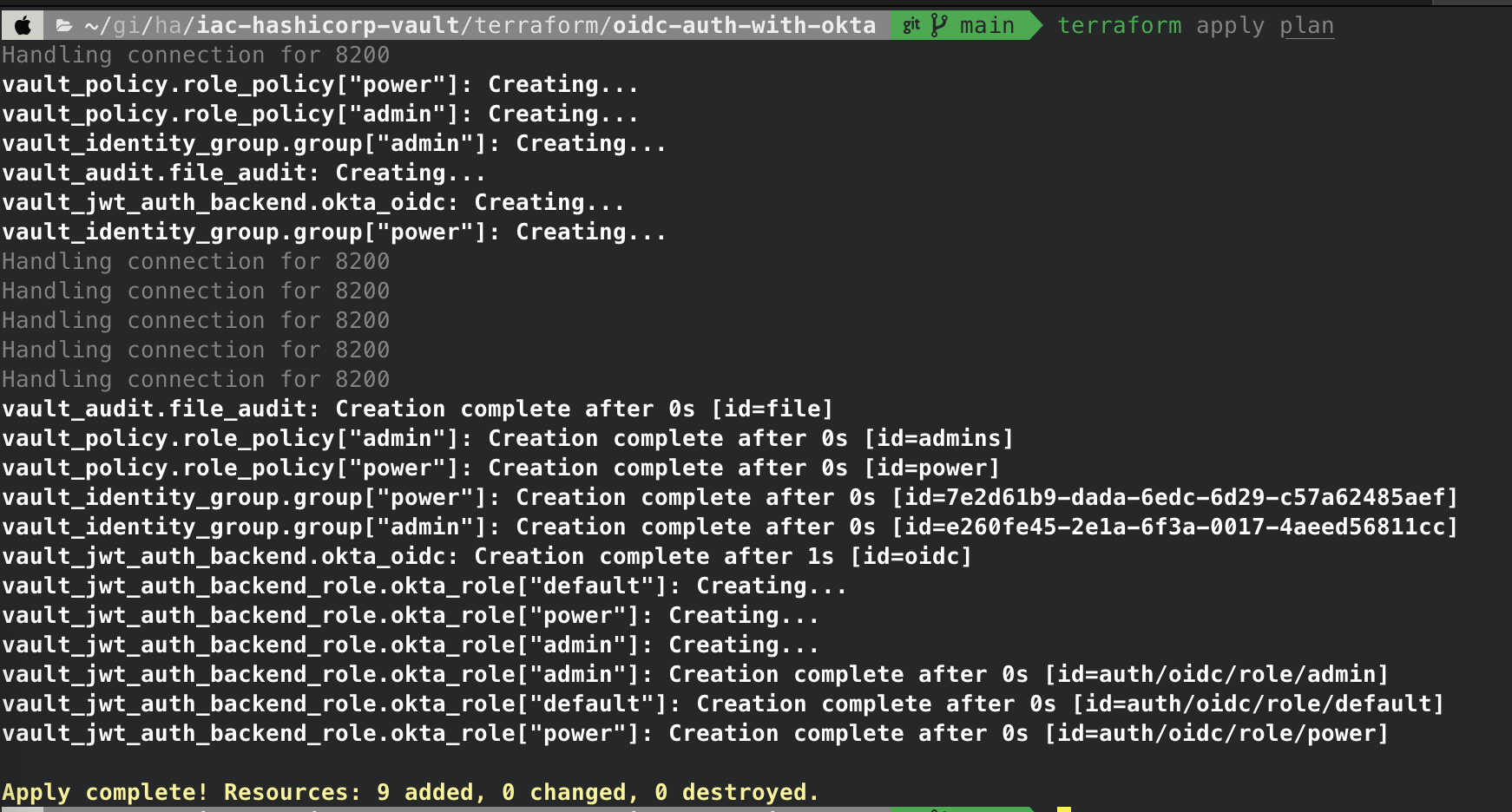
You’re now set up to log into Vault with Okta.
Log in to Vault with Okta
You can now log in with OIDC, specifying which role you want to assume. Try it with: admin or power.
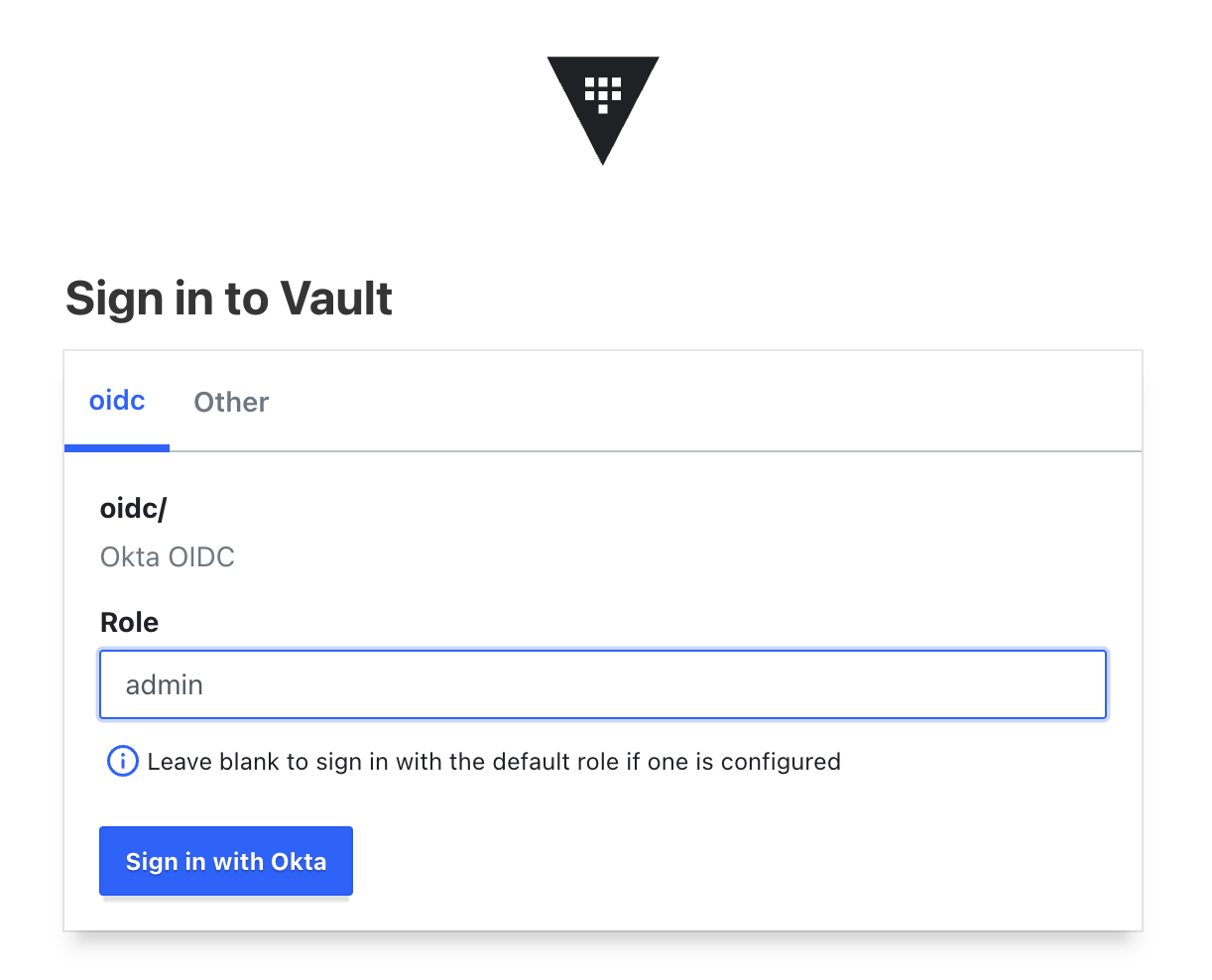
Alternatively, log in via the CLI: vault login -method=oidc role="admin"
Clean up
Uninstall Vault with helm (optional) and destroy the kind cluster: ./destroy.sh